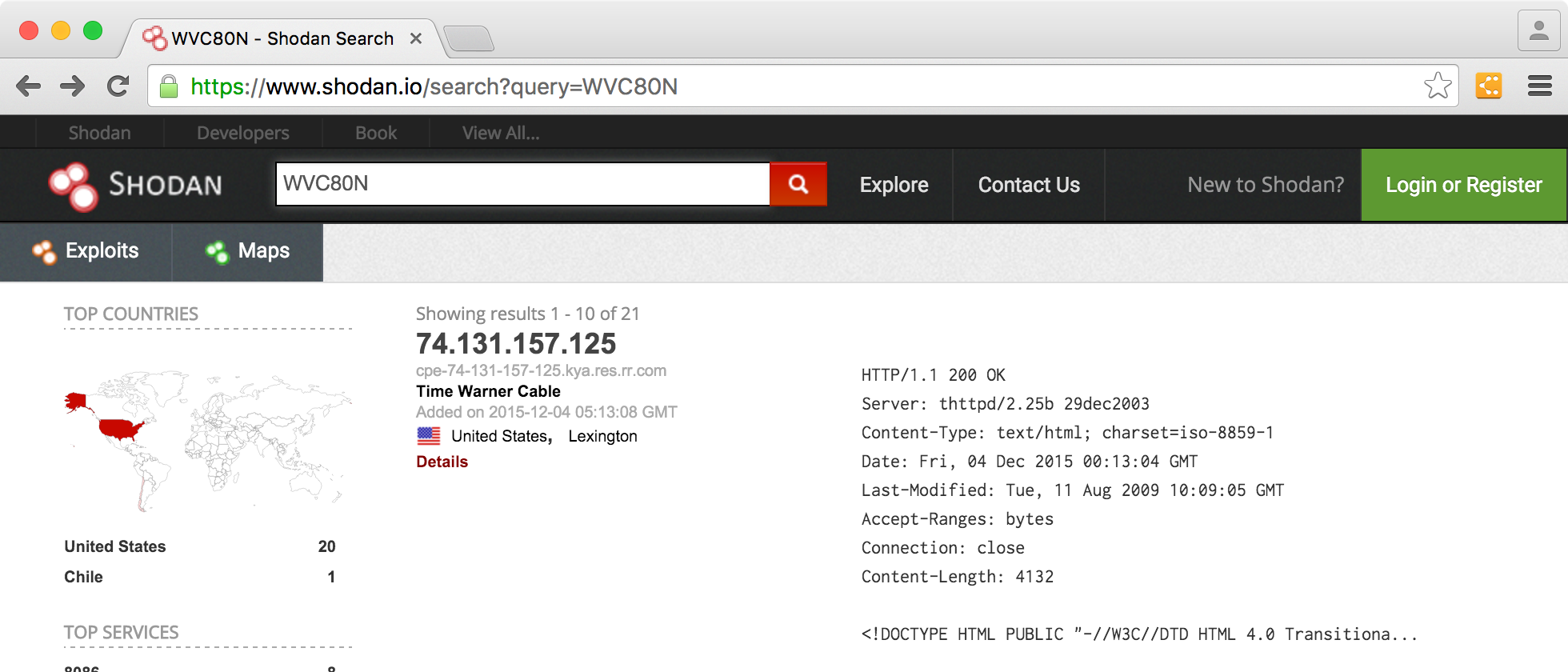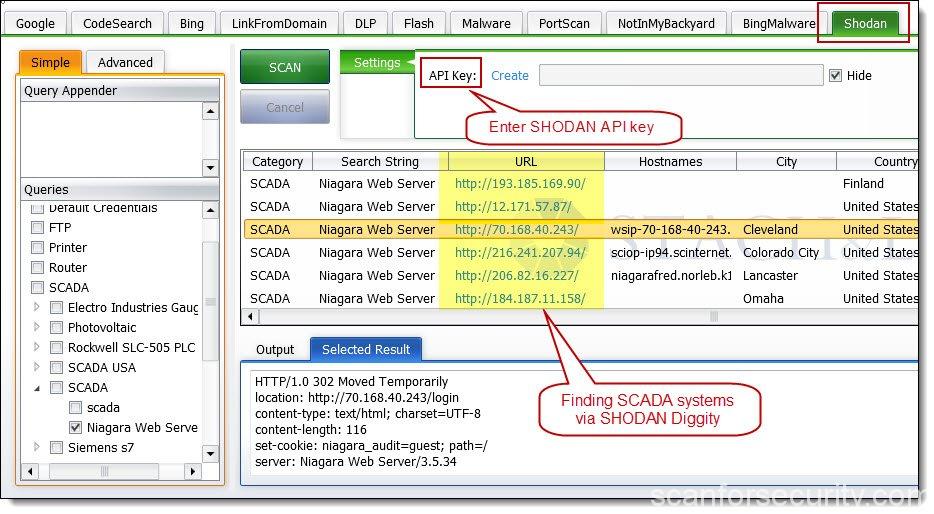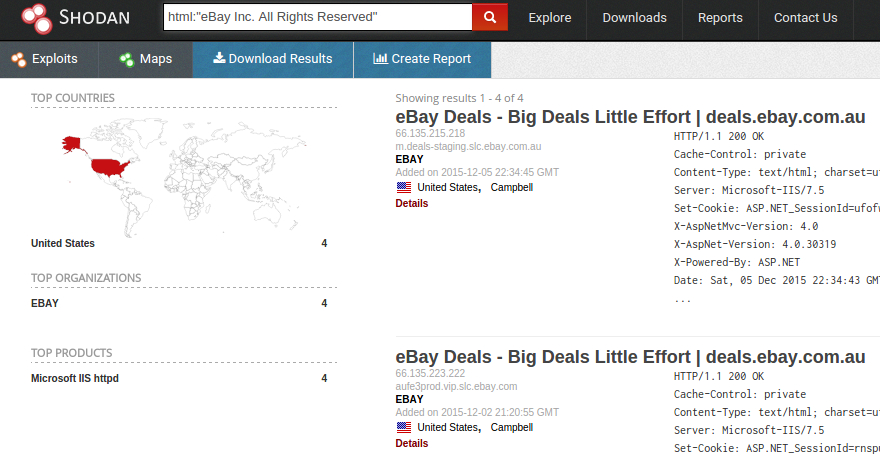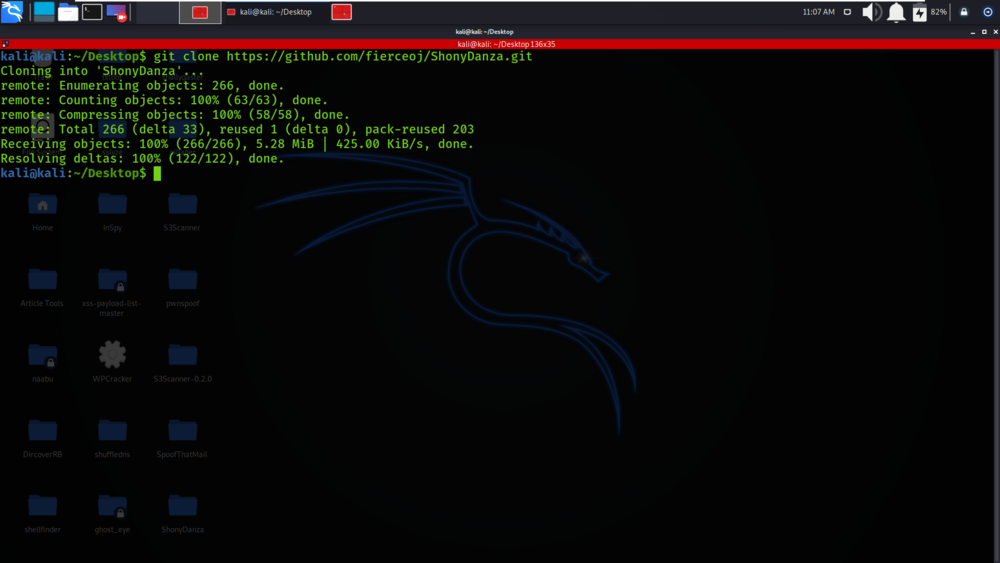
ShonyDanza - Tool For Researching, Pen Testing, And Defending With The Power Of Shodan - GeeksforGeeks
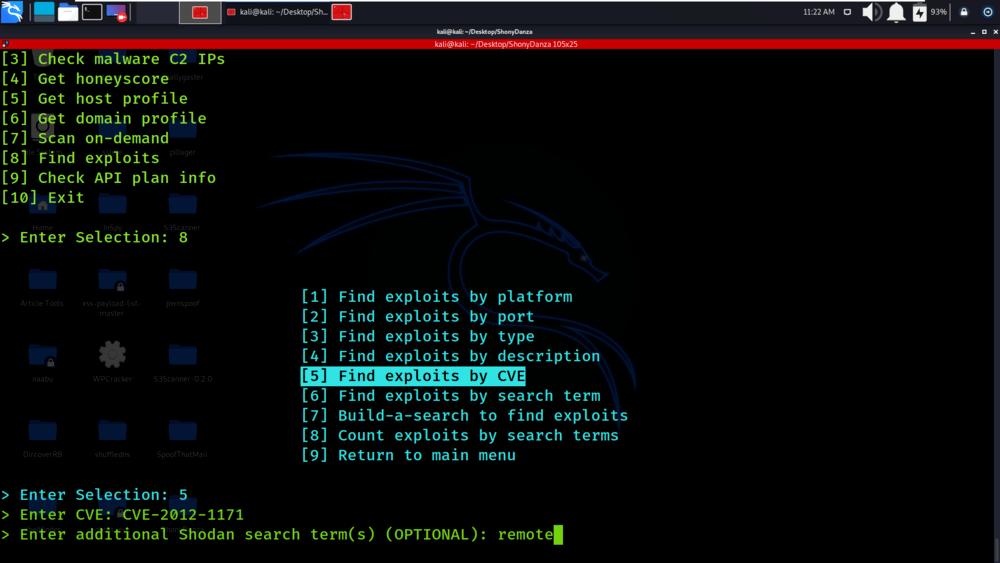
ShonyDanza - Tool For Researching, Pen Testing, And Defending With The Power Of Shodan - GeeksforGeeks
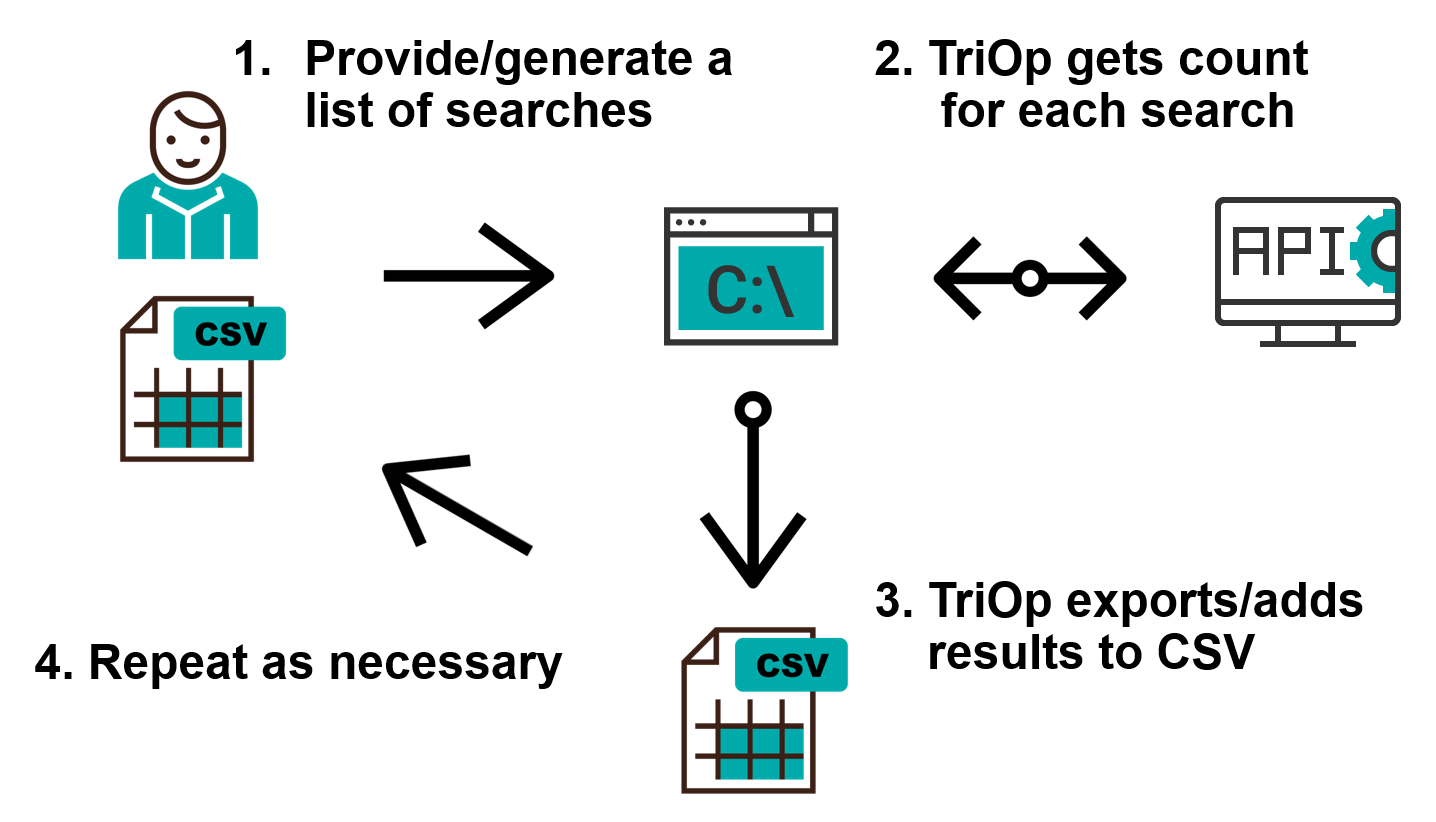
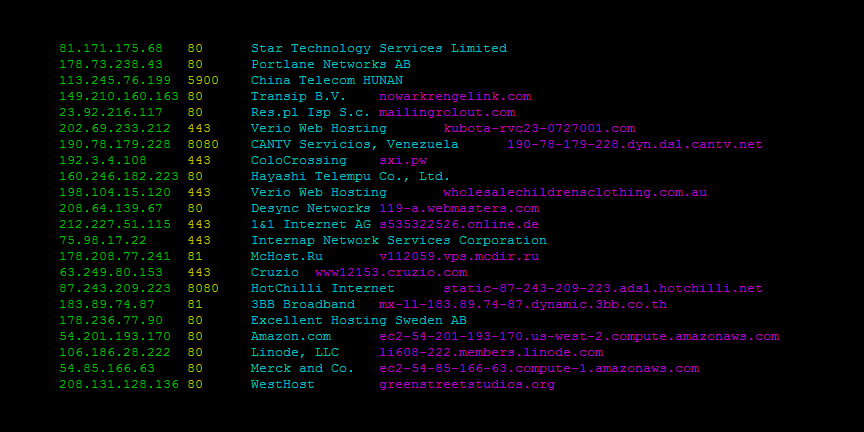
TriOp - tool for gathering (not just) security-related data from Shodan.io ( tool drop) - SANS Internet Storm Center
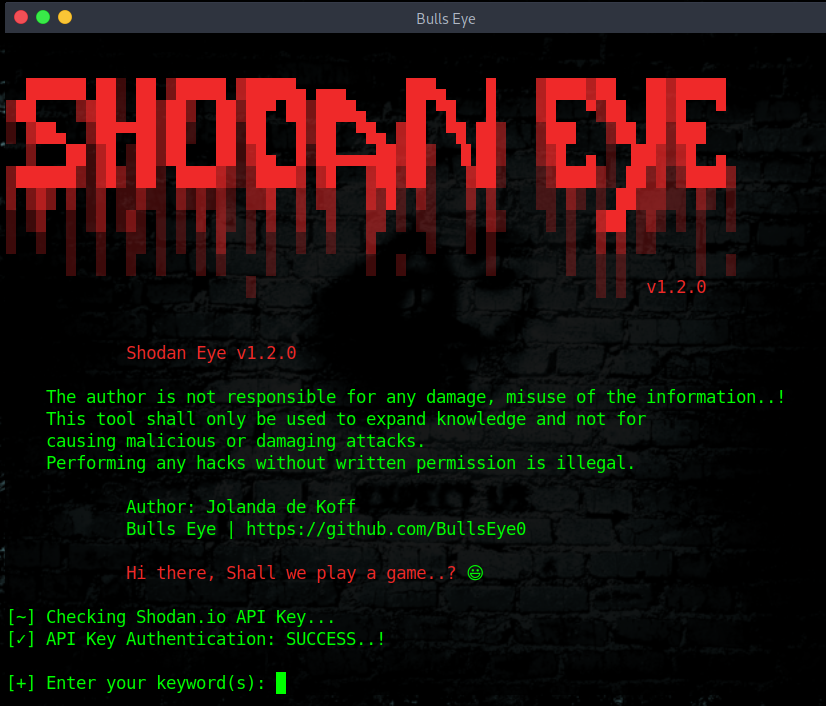
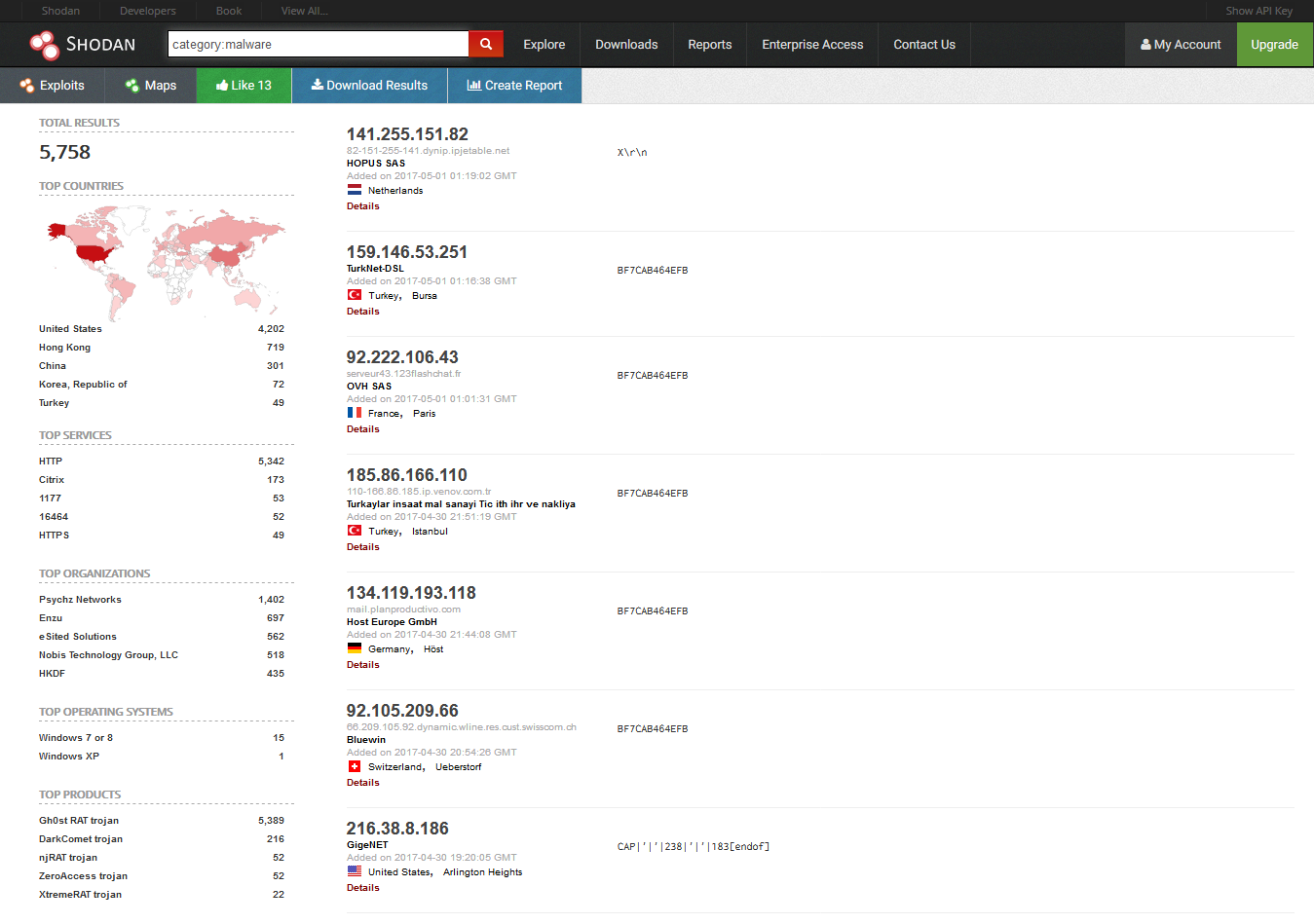
Shodan-Eye - Tool That Collects All The Information About All Devices Directly Connected To The Internet Using The Specified Keywords That You Enter

OSINT Cracking Tools: Maltego, Shodan, Aircrack-Ng, Recon-Ng: Botwright, Rob: 9781839386084: Amazon.com: Books
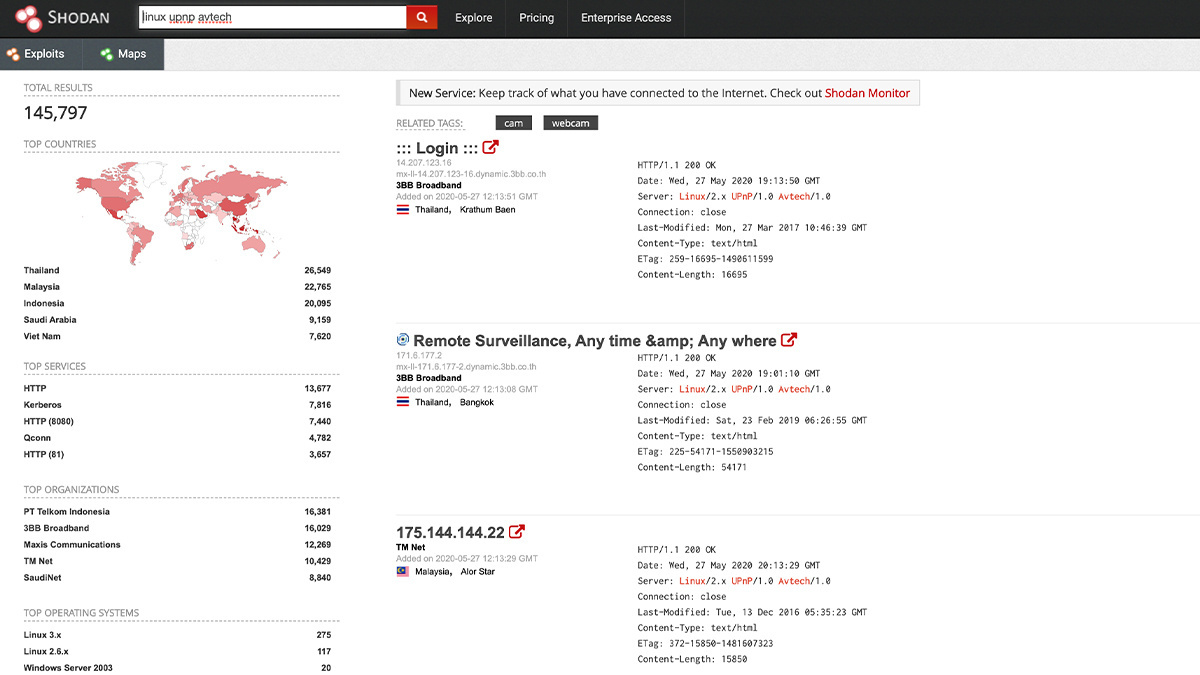
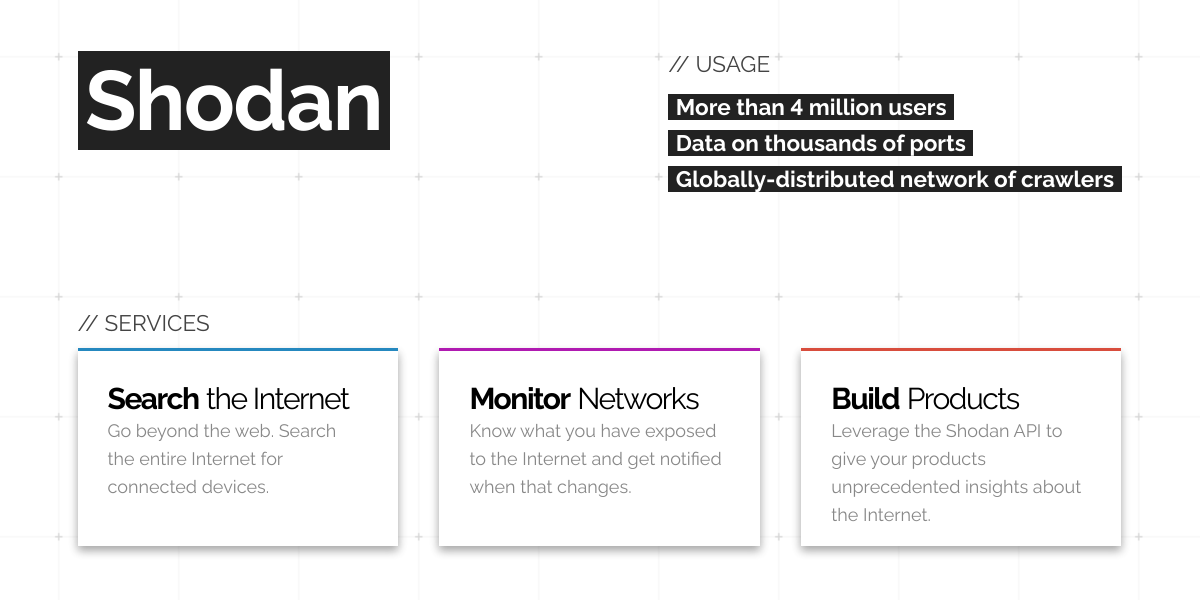
Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig

Bestech Shodan BT1910B Black Stonewash couteau de poche, Todd Knife & Tool design | Achetez à prix avantageux chez knivesandtools.fr

Bestech Shodan BT1910B Black Stonewash couteau de poche, Todd Knife & Tool design | Achetez à prix avantageux chez knivesandtools.fr