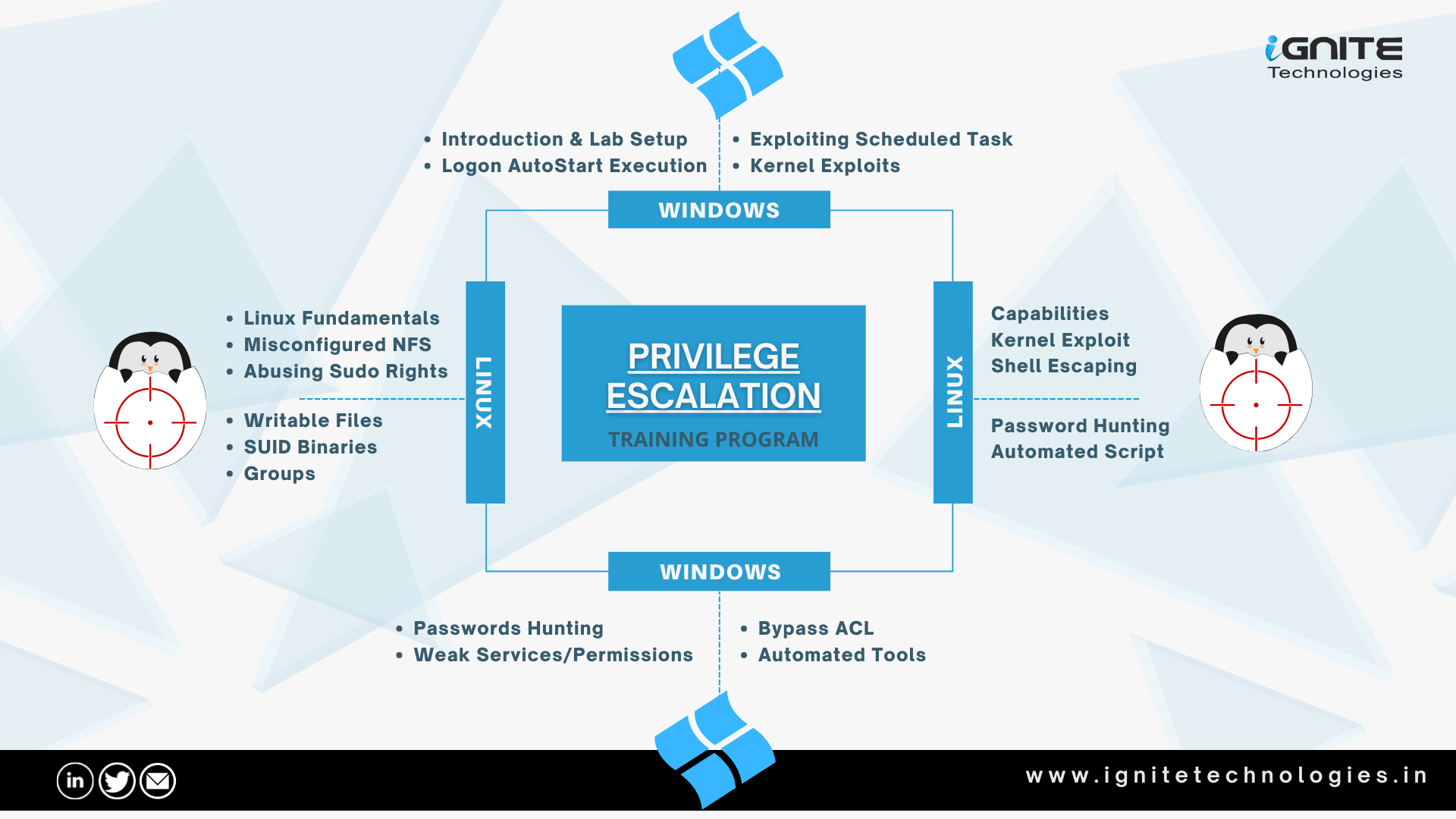
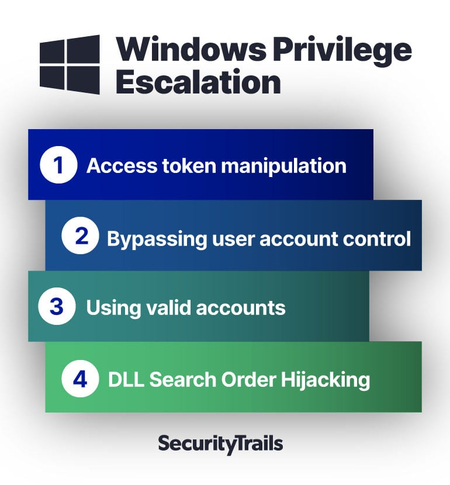
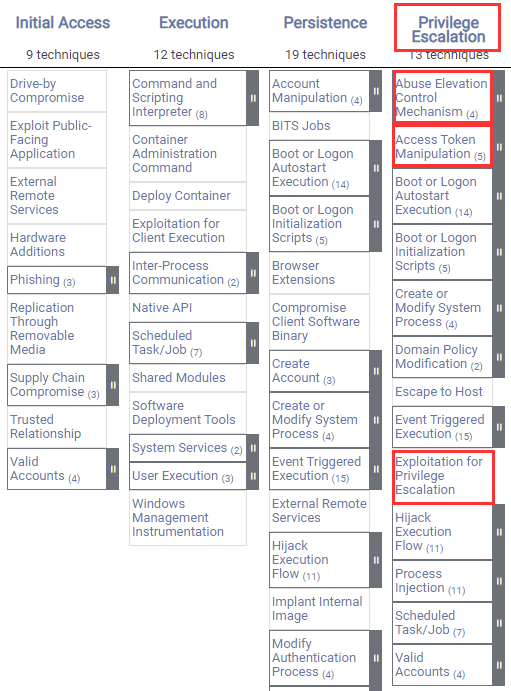
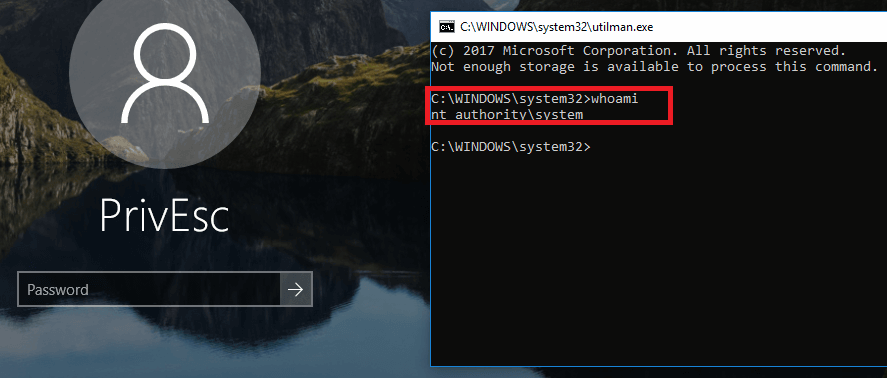
TryHackMe — Jr Penetration Tester | Privilege Escalation | Linux Privesc | Part 2 | by Aditya Sharma | Medium

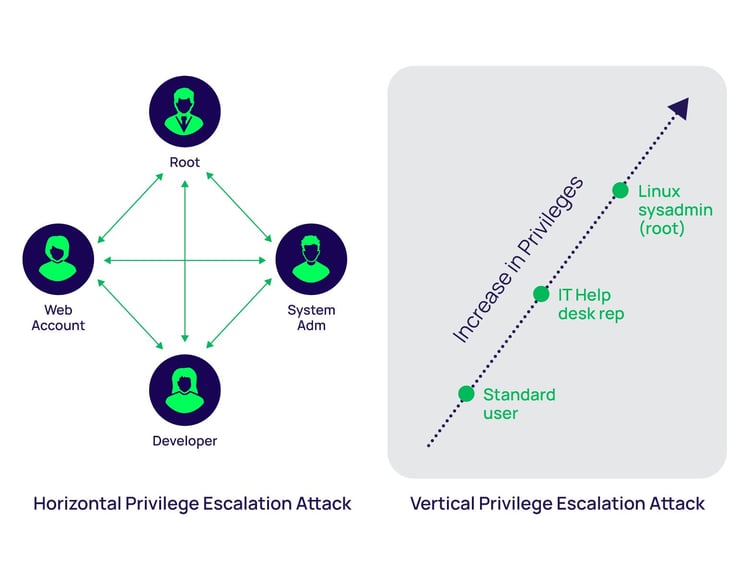
Hacking Articles on X: "Privilege Escalation Tools #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips ...
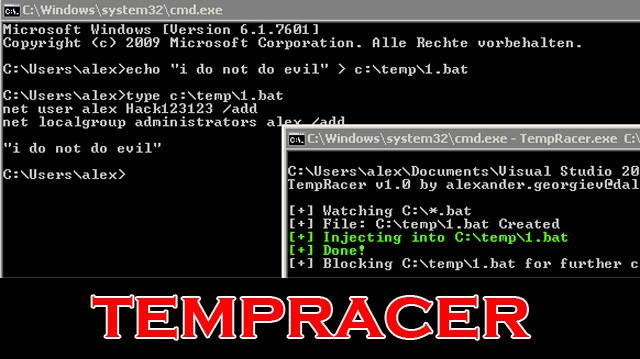
TempRacer - Windows Privilege Escalation Tool - Darknet - Hacking Tools, Hacker News & Cyber Security

Linux Exploit Suggester - Linux Privilege Escalation Auditing Tool - Kali Linux 2018.1 – PentestTools