The Automotive Threat Modeling Template | NCC Group Research Blog | Making the world safer and more secure
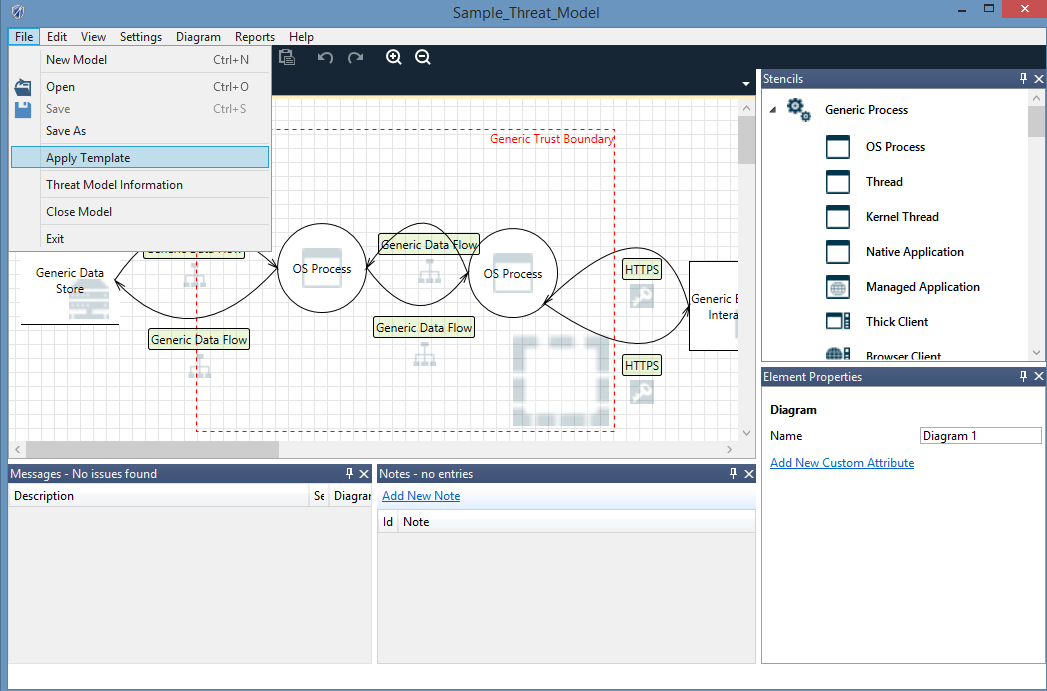
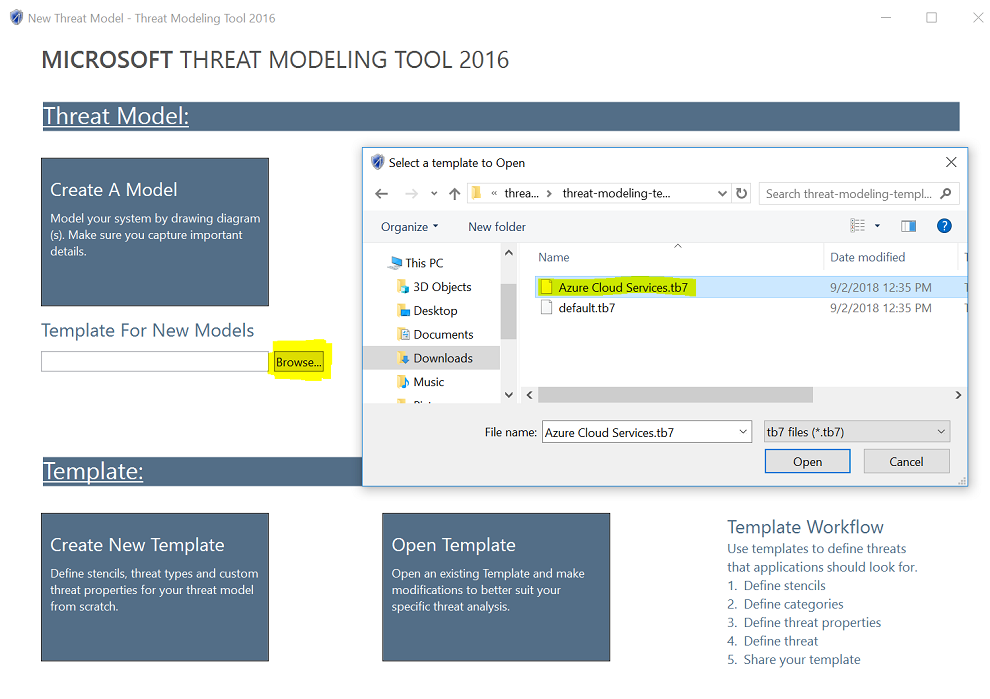
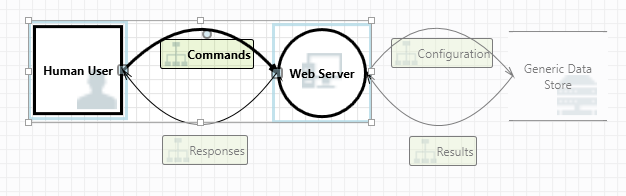
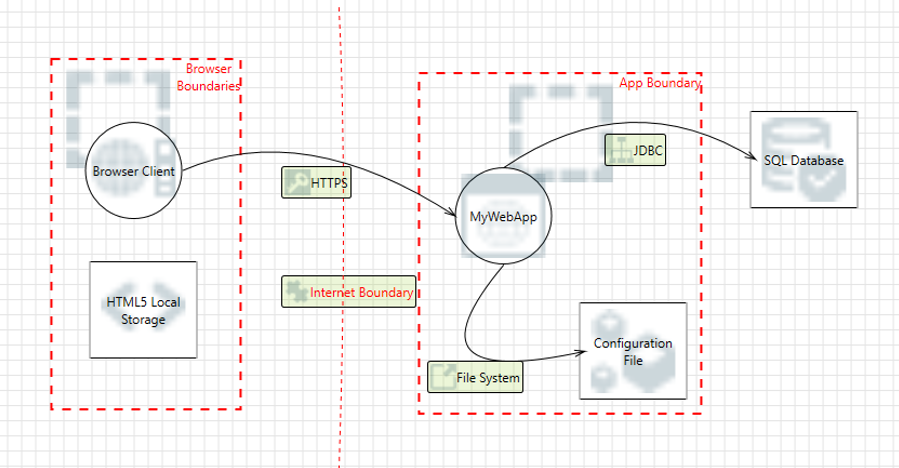
Give a complete example (using two applications one from Application 1 and another from Application 2 listed inword named applications)your end results are the list and description of risk found .You
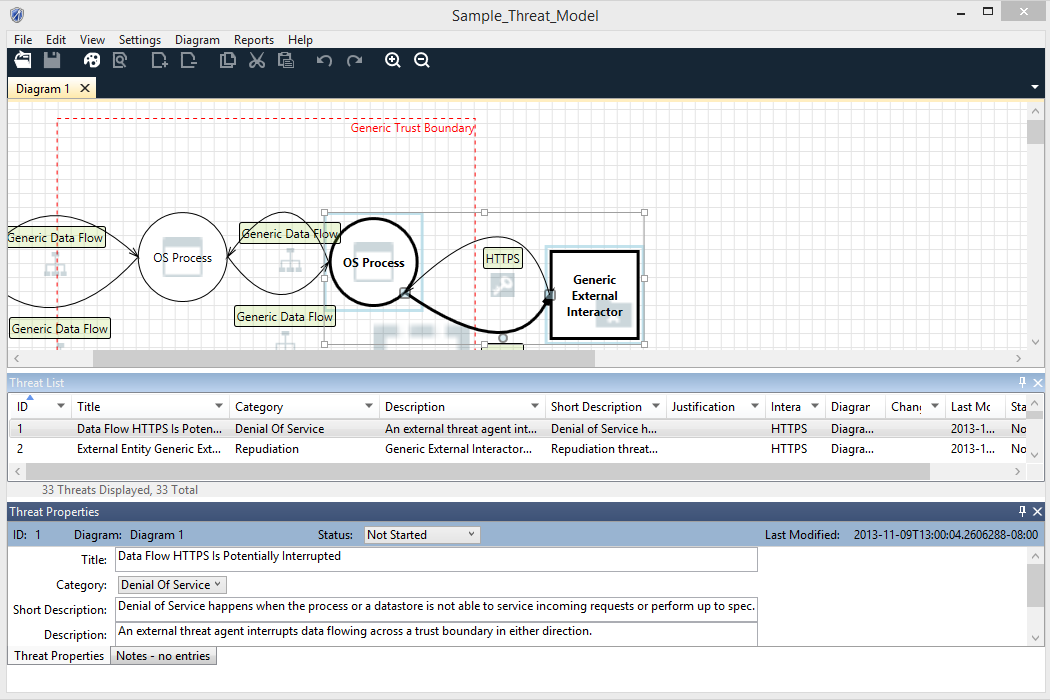
Give a complete example (using two applications one from Application 1 and another from Application 2 listed inword named applications)your end results are the list and description of risk found .You
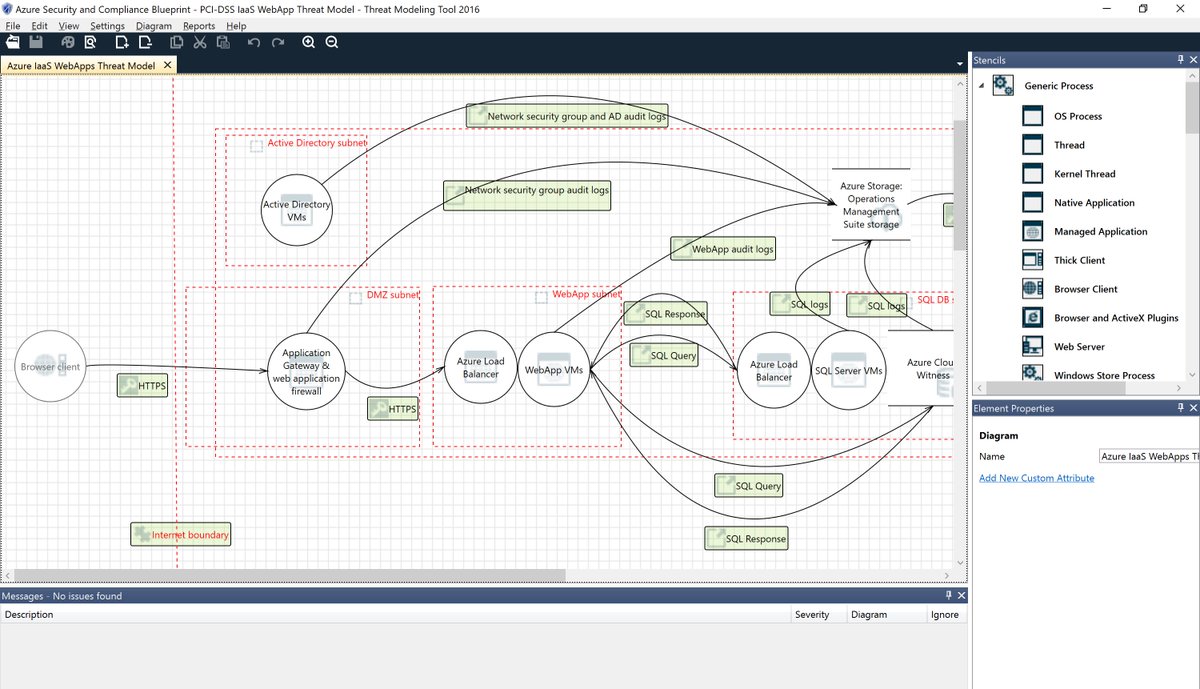
Lennart Passig on X: "Use the #Microsoft #Threat #Modeling #Tool 2016 that helps you finding threats in the design phase of software projects! Very good product after the first initial glance at
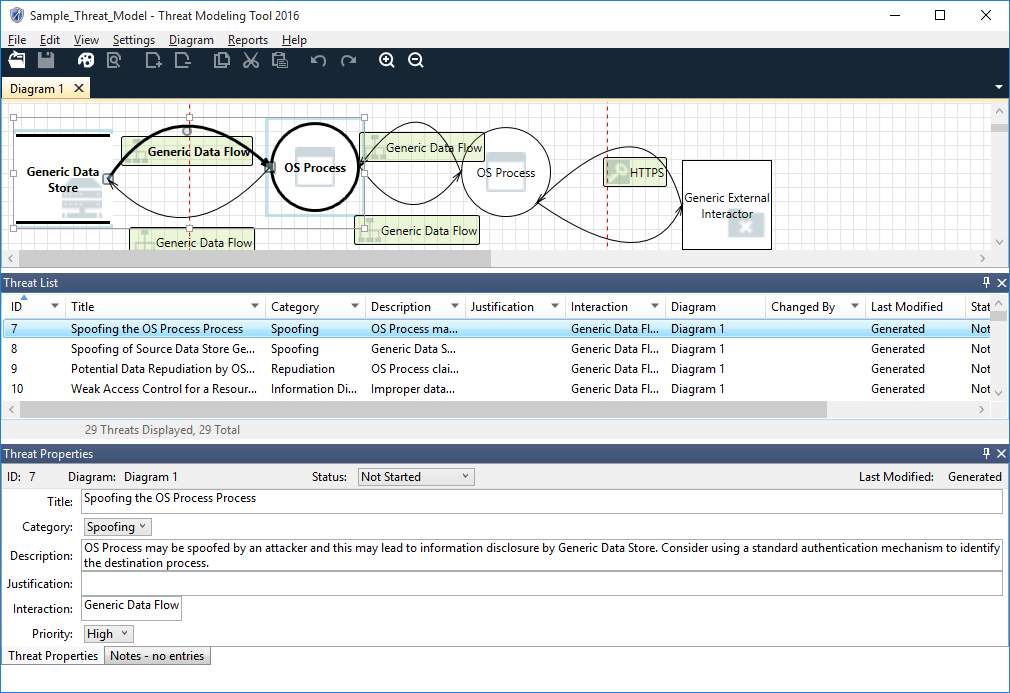
Microsoft Stories and News on X: "What's new with Microsoft Threat Modeling Tool 2016 http://t.co/YrD03l2KUH http://t.co/GFOIVcb1py" / X
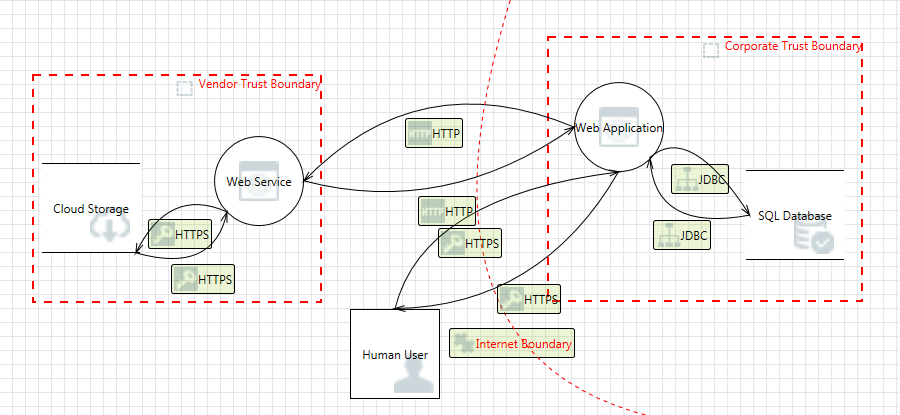
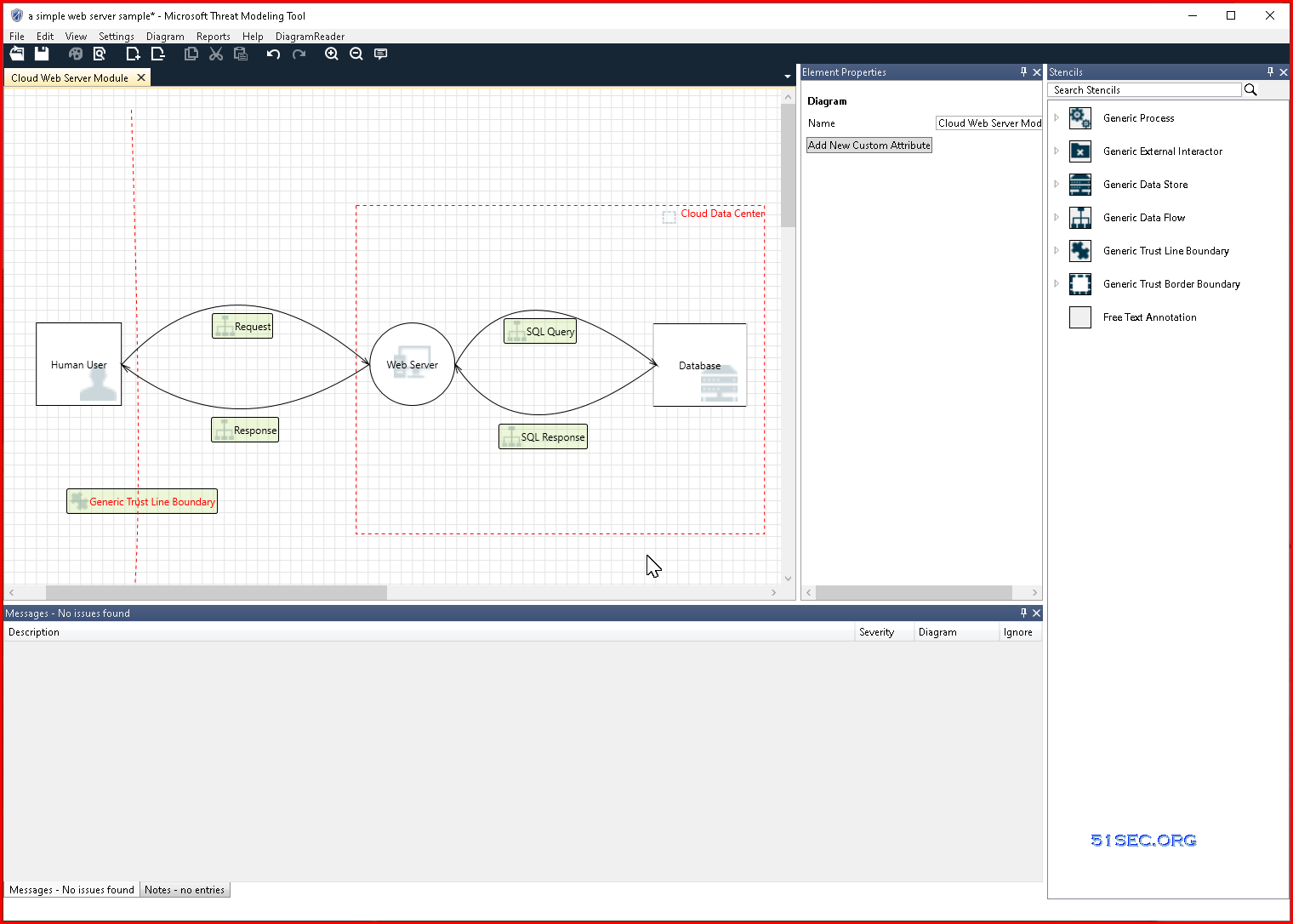
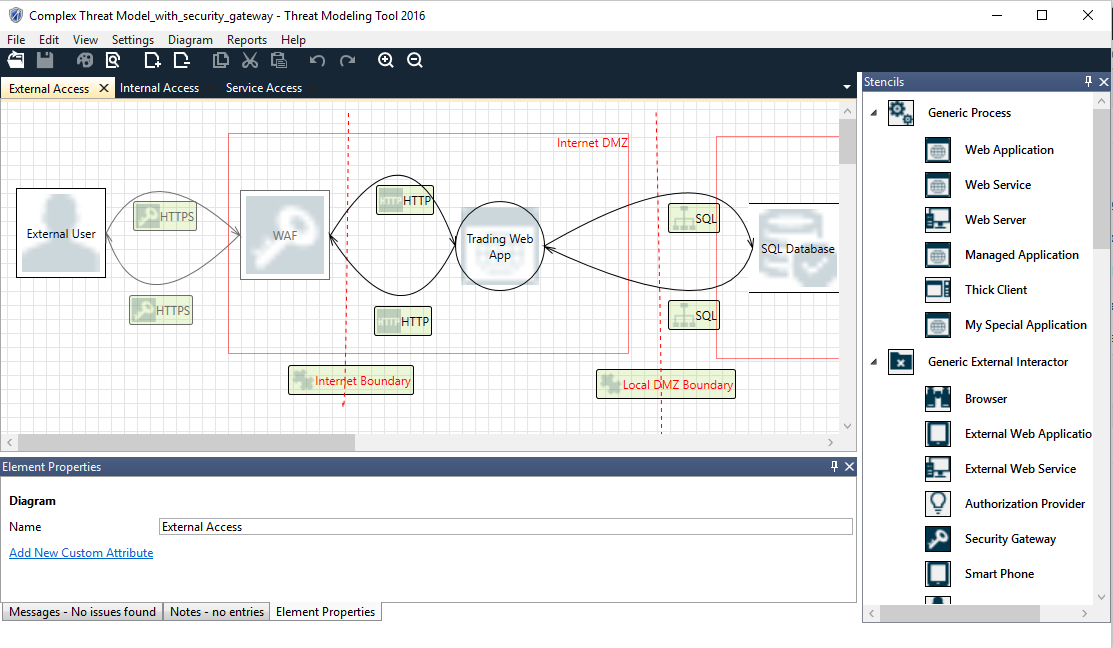










![Microsoft Threat Modeling Tool - Network Vulnerability Assessment [Book] Microsoft Threat Modeling Tool - Network Vulnerability Assessment [Book]](https://www.oreilly.com/api/v2/epubs/9781788627252/files/assets/385cf454-2055-42d5-9aae-f1bda0e424be.png)